Intensifying Data and Information Security
Through Digitalization

First Gen manages its information and technology infrastructure in a secure and effective manner, combined with industry comprehension, organizational systems, specialized skills, and expertise. Our processes and systems continue to shift towards digital interfaces and automation, which directly impacts security of data and information and the effective carry-out and monitoring of work deliverables with our hybrid ways of working.
Threats and vulnerabilities were determined through risk assessments done annually. Several solutions and programs that would address these threats and improve our business operations were implemented. Our Information Technology Governance Council (ITGC) is responsible for prioritizing and approving information technology investments and projects. The ITGC also ensures the effective delivery of IT value and the alignment of these benefits with Company priorities. The IT Group is responsible for the acquisition, development, dissemination, and implementation of IT solutions, projects, and policies. It is also responsible for employing solutions based on business needs, best-fit practices, and technological innovations.
First Gen invested USD6.4 million for digitalization and automation, cyber, and information security, with the 15.6 percent increase from the USD5.4 million investment in 2022.

Our information security processes and programs are governed by our Information Security Governance Committee (ISGC) headed by our Chief Information Security Officer. The ISGC provides the senior management an assurance that information security direction and intent are reflected in the security posture of the organization by utilizing a structured approach to implementing an information security program. Anchoring from our Information Security Policy approved in 2019, 24 new processes and procedures were initiated to intensify our information security: infosec awareness, phishing mindfulness, use of removable media, InfoSec incident management, infosec security management, network access control, firewall, password and IT security. With the influx of Internet of Thing (IoT) devices, our IT Group governs IoT devices to help ensure that these meet technology/security standards; and implemented creation of inventory, patching/updating, and monitoring. To mitigate the incursion of artificial intelligence (AI) tools/applications, several awareness campaigns were conducted to employees, InfoSec and IT policies developed and maintained, and continued consultations with industry experts. Moreover, we established our Information Security Management System (ISMS) through the strategy below.
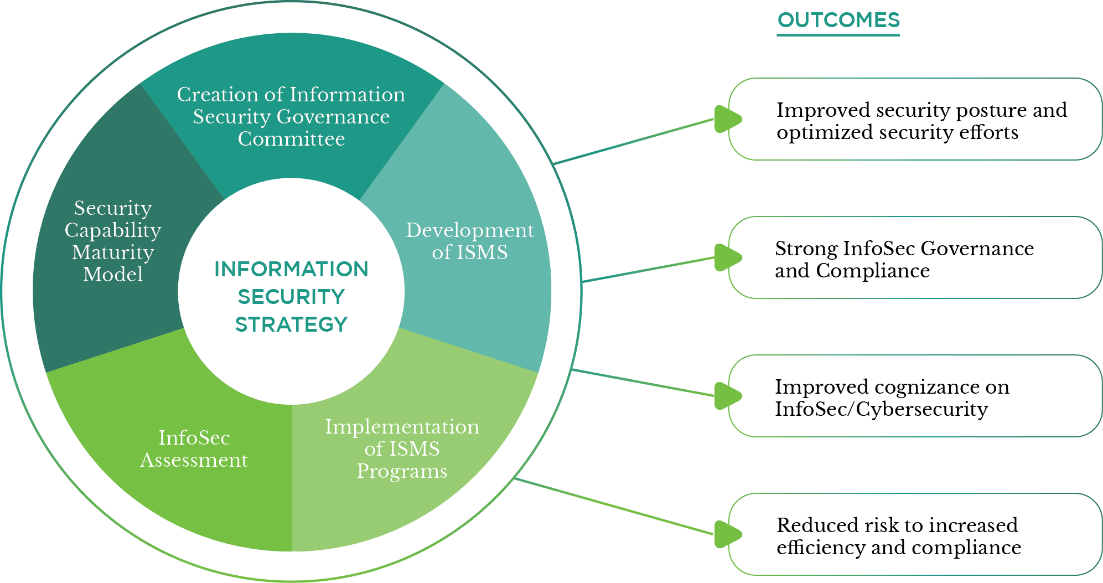

Programs implemented through our ISMS include InfoSec awareness program, online assessment, online training including our third party partners, phishing test campaign, awareness ecards and logs, advisories and Infosec month celebration. Infosec assessments include vulnerability assessment and penetration testing, the software and hardware we utilize, and our processes.
To further strengthen security and data privacy, we started the Phase 1 implementation of the Records Management System. Information within First Gen is classified as either restricted, confidential, internal use, or public. All information outside of the public domain is considered sensitive information and covered by the Information Security Policy. As a primary means of sharing sensitive information with contractors and partners, contracts and other forms or agreements with our contractors and partners are covered by non-disclosure agreements. First Gen also values the confidentiality of personal data. Thus, a Privacy Notice posted on our website details how the Company uses and protects personal data in accordance with the Data Privacy Act of 2012 (DPA), its IRR, other issuances of theNational Privacy Commission (NPC), and other relevant laws of the Philippines. This Privacy Notice can be accessed through this link: https://www.firstgen.com.ph/privacy . There was no data breach or violation of informational privacy rights or any other violation of the DPA cited.